Last Updated: December 16, 2015
WordPress Total Security Vulnerability Test tutorial will show you how to read and troubleshoot any finding the plugin reveals when you scan for vulnerabilities.
Latest News: I have added another link to the menu.
This plugin has a great search mechanism for website vulnerabilities. When you first install it you need to run the vulnerability check. This check will reveal any findings on your website and provide ways for you to fix and or troubleshoot the findings.
In this post I will show you how to correctly read those findings and how to fix them as well. Some options are for advance users however if you are careful and are confident, you should be able to fix it yourself.
Note: Always backup your website and especially your database before you edit and or make any changes.
WordPress Total Security Plugin Tutorials
- Total Security Plugin
- Vulnerability Test
- File System Check
- Settings
- Troubleshooting
WordPress Total Security Vulnerability Test Steps
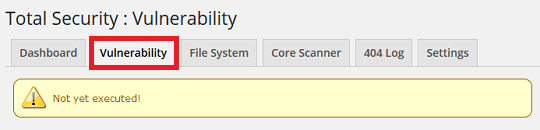
Step 1 ) The following image Total Security : Vulnerability allows shows you that you have not yet executed a test yet. This means that this is the first time you run this step in the plugin.
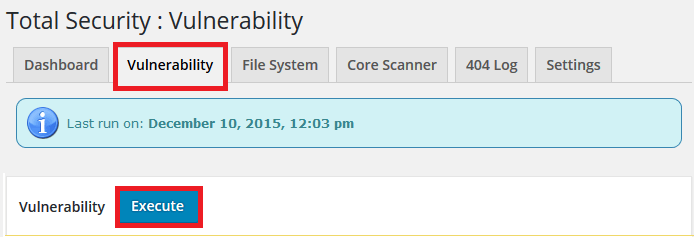
Step 2 ) The following image illustrates the last time a test was executed. In this example it says December 10, 2015, 12:03 pm. (In your website the date will be different.)
If you need to run or did not run the test, simply click on Execute button to run the test.
Step 3 ) The following is an example image that shows you some of the findings. If you see a Green tick next to one of the test you know it has passed the test. If you see a Blue tick then you need to investigate further and you will see a Yes in blue for you to click on. The same applies for Orange and Red ticks. In some areas you will see different links, for example in file permissions. If one of your settings is 777 then you will see a link on that number.
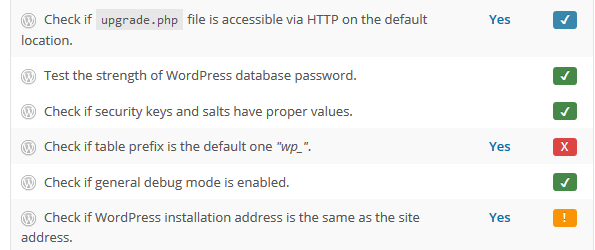
The following are all the checks it carries out when you execute the vulnerability test.
WordPress Security Checks
- Check if WordPress core is up to date.
- Check if plugins are up to date.
- Check if themes are up to date.
- Check if install.php file is accessible via HTTP on the default location.
- Check if upgrade.php file is accessible via HTTP on the default location.
- Test the strength of WordPress database password.
- Check if security keys and salts have proper values.
- Check if table prefix is the default one “wp_”.
- Check if general debug mode is enabled.
- Check if WordPress installation address is the same as the site address.
- Check if uploads folder is browsable by browsers.
- Check if “anyone can register” option is enabled.
- Check if plugins/themes file editor is enabled.
- Check if user with username “admin” exists.
- Test if user with “ID=1” is administrator.
- Check admin password strength with a 1050 most commonly used.
- Check if “Secure Hidden Login” is enabled.
Server Configuration
- MySQL Version
- PHP Version
- PHP max_execution_time
- PHP Memory Limit
- PHP allow_url_include
- PHP allow_url_fopen
- Dangerous PHP Functions
File Permissions – chmod
- /
- wp-admin
- wp-content
- wp-includes
- .htaccess
- index.php
- wp-config.php
- wp-blog-header.php
Click on the following URL File System Check to continue with the settings.
I will be updating this post from time to time. So keep coming back for more.
Enjoy