All In One Security Firewall Rules Settings helps you setup the following options basic firewall rules, disable index view and much more.
Last Updated: March 11, 2024
Latest News: Updated the document.
This post provides information about the different Firewall protection options you can enable to protect your website. These settings are important but at the same time they can cause issues in your site. I recommend that you read each feature carefully before you enable it.
Steps you should take when enabling Firewall features. Start by enabling one by one each feature and at the same time carry out a test. Do this with all the features until you are happy with the features you have enabled. Too many keep running into issues when they enable most or all Firewall rules.
Important Note
This plugin has so many firewall rules which are deliberately split up into separate sections. Not all sites will work 100% with all of the rules enabled due to the fact that every site has a unique setup.
In some cases you will have to disable the feature that is causing issues in your site. As a general rule of thumb: if you had to choose just one firewall rule it would be the 6G rules because it provides the best all-round coverage/protection.
What you need:
All In One Security Firewall Rules Settings
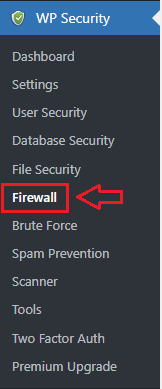
Step 1 ) Go to WP Security -> Firewall admin sidebar menu as illustrated in the image below.
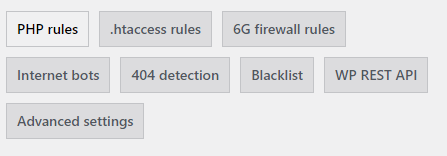
Step 2 ) The following image Firewall admin tabs allows you to set up the following security settings. Please carefully read each Firewall feature before you activate it.
Firewall Settings Tabs
- PHP rules
- .htaccess rules
- 6G firewall rules
- Internet bots
- 404 detection
- Blacklist
- WP REST API
- Advanced settings
PHP rules
Step 3 ) Click on WP Security -> Firewall -> PHP rules to set up the following security settings.
Note: To learn more about this feature check the following URL All In One WP Security Plugin Pingback Protection Settings.
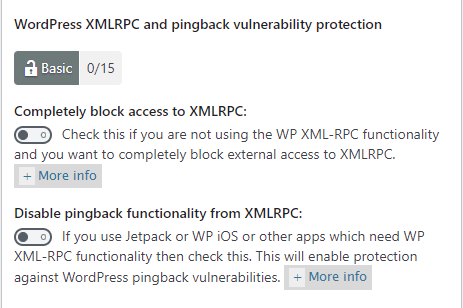
WordPress XMLRPC and pingback vulnerability protection options
- Completely block access to XMLRPC:
- Disable pingback functionality from XMLRPC:
If you enable these options, it will add another 15 points score towards your security meter. (Basic Security Level)
===============================
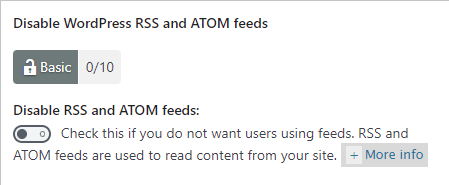
Step 3-a ) The following image Disable WordPress RSS and ATOM feeds allows you to set up the following security setting.
Disable WordPress RSS and ATOM feeds option
- Disable RSS and ATOM feeds:
If you enable this option, it will add another 10 points score towards your security meter. (Basic Security Level)
===============================
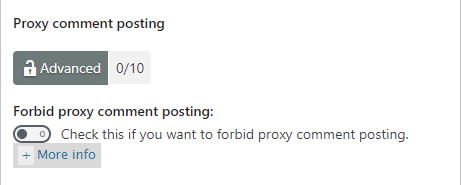
Step 3-b ) The following image Proxy comment posting allows you to set up the following security settings.
Proxy comment posting option
- Forbid proxy comment posting: (Note: If you experience any issues and you happen to be using a CDN i.e. Cloudflare, then disable this feature. Check the following forum post to learn more.)
If you enable this option, it will add another 10 points score towards your security meter. (Advanced Security Level)
===============================
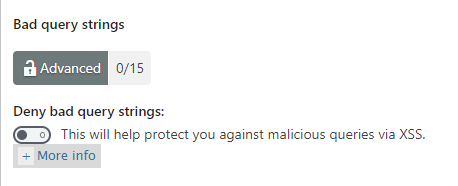
Step 3-c ) The following image Bad query strings allows you to set up the following security settings.
Bad query strings option
- Deny bad query strings: = Note: See troubleshooting note below.
If you enable this option, it will add another 15 points score towards your security meter. (Advanced Security Level)
===============================
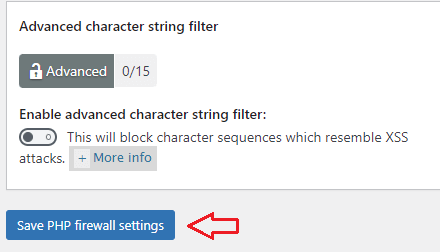
Step 3-d ) The following image Advanced character string filter allows you to set up the following security settings.
Advanced character string filter option
- Enable advanced character string filter
- Click on Save PHP firewall settings button when you complete your settings.
If you enable this option, it will add another 15 points score towards your security meter. (Advanced Security Level)
Troubleshooting Deny Bad Query Strings
In some sites this feature might not work and trigger some error messages. If that is the case you can leave “Bad Query Strings” rules disabled or you can modify them by figuring out which string is causing the trigger. Then all you have to do is copy and paste the modified rules in the custom rules section.
In general if you had to choose only one set of firewall rules to enable, it would be the 6G rules because they are the best all-round .htaccess firewall rules.
===============================
.htaccess rules
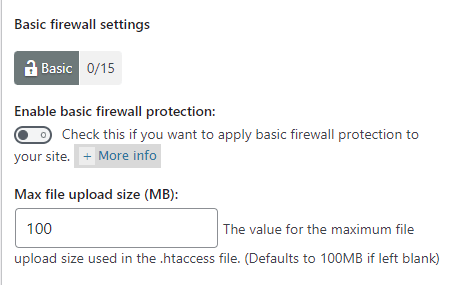
Step 4 ) Click on WP Security -> Firewall -> PHP rules to set up the following security settings.
Basic firewall settings options
- Enable basic firewall protection:
- Max file upload size (MB):
If you enable this option, it will add another 15 points score towards your security meter. (Basic Security Level)
Troubleshooting Basic Firewall Settings
Q1 I receive the following message “The plugin was unable to write to the .htaccess file” when I click on the save button in “Save Basic Firewall Settings”. How can I fix this issue?
Answer: For a possible solution you need to check your server configuration settings. Please check the following forum post to learn more.
===============================
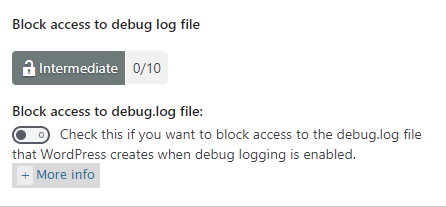
Step 4-a ) The following image Block access to debug log file allows you to set up the following security settings.
Block access to debug log files option
- Block access to debug.log file:
- Click on Save Basic Firewall Settings button when you complete your settings.
If you enable this option, it will add another 10 points score towards your security meter. (Intermediate Security Level)
===============================
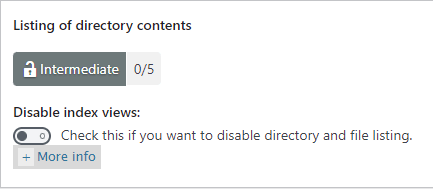
Step 4-b ) The following image Listing of directory contents allows you to set up the following security settings.
Listing of directory contents option
- Disable index views:
If you enable this option, it will add another 5 points score towards your security meter. (Intermediate Security Level)
===============================
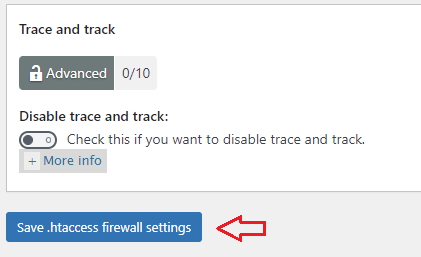
Step 4-c ) The following image Trace and track allows you to set up the following security settings.
Trace and track option
- Disable trace and track:
- Click on Save .htaccess firewall settings button when you complete your settings.
If you enable this option, it will add another 10 points score towards your security meter. (Advanced Security Level)
===============================
6G firewall rules
Step 5 ) Click on WP Security -> Firewall -> 6G firewall rules to activate one of the following security settings.
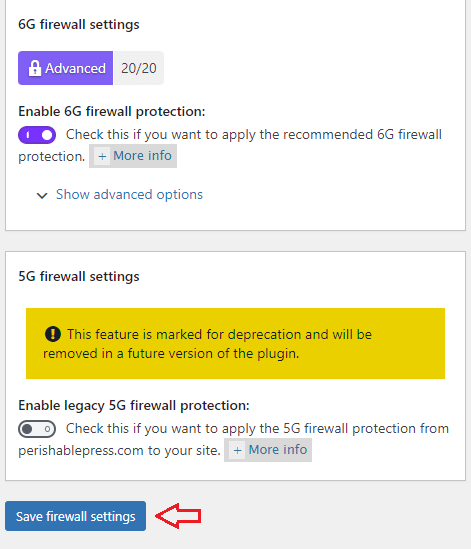
Warning: You cannot enable both options at the same time. This would cause a conflict.
The 6G firewall protection feature below protects your site against many exploits, including sql injections and more. The developers have written an extensive documentation describing what it protects. You can read more about it from the following URL 6G Firewall 2017.
6G firewall settings options
- Enable 6G firewall protection:
- Enable legacy 5G firewall protection: (Note: This option should not be enabled anymore. 6G is much better. The plugin developers will be removing this option soon.)
- Click on Save firewall settings button when you complete your settings.
If you enable this option, it will add another 20 points score towards your security meter. (Advanced Security Level)
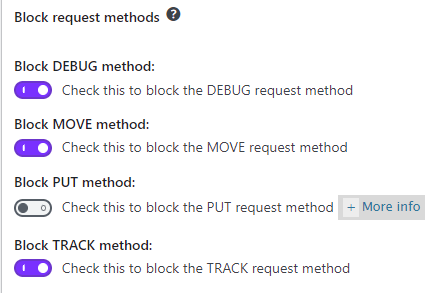
Step 5-a ) The following image 6G Block request methods allows you to configure the following options.
6G Block request methods settings
- Block DEBUG method:
- Block MOVE method:
- Block PUT method:
- Block TRACK method:
- Click on Save request methods settings button when you finish completing your settings.
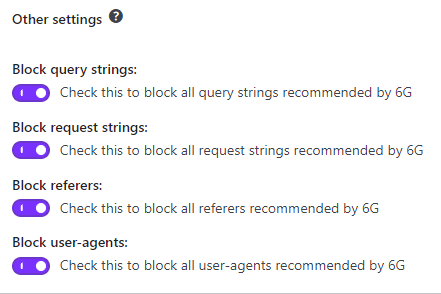
Step 5-b ) The following image 6G other settings allows you to configure the following options.
6G other settings
- Block query strings:
- Block request strings:
- Block referrers:
- Block user-agents:
- Click on Save other settings button when you finish completing your settings.
Questions and Troubleshooting 6G Blacklist Firewall Rules
Q1 Does the plugin protect against SQL Injections?
Answer: Yes, enabling 6G Blacklist Firewall Rules will protect you against sql injections and more.
Note: As far as secure coding practices, this plugin is coded such that any user input it sends to the DB is securely sanitised and escaped against SQL injection attacks.
Having said that, you should be careful regarding which plugins you install on your site and make sure that you get them from reputable sources because not all plugins will have safe coding practices. (Note provided by wpsolutions in the forum)
=====================
Q2 6G rules is blocking Cloudflare plugin JavaScript, how do I fix this issue?
Answer: Check the following forum post for a solution provided by Chris J. Zähller.
===============================
Internet bots
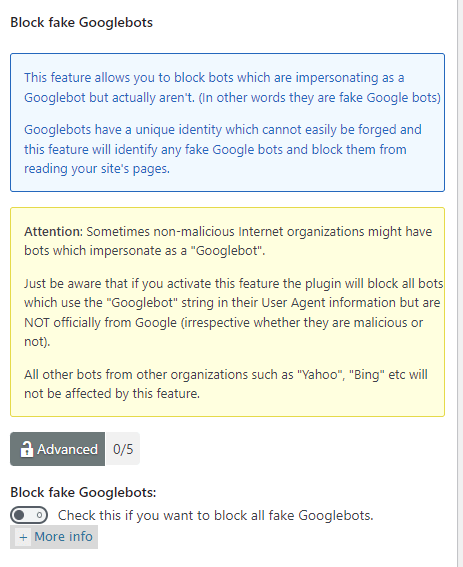
Step 6 ) Click on WP Security -> Firewall -> Internet bots allows you to set up the following security settings.
Internet bots settings
- Block fake Googlebots:
If you enable this option, it will add another 5 points score towards your security meter. (Advanced Security Level)
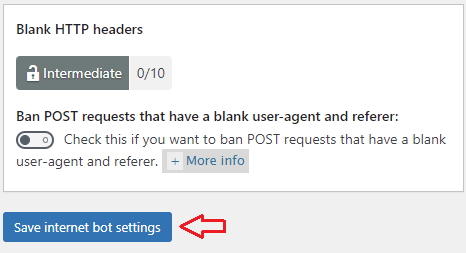
Step 6-a ) The following image Blank HTTP headers allows you to setup the following option.
Blank HTTP headers settings
- Ban POST requests that have a blank user-agent and referer:
- Click on Save internet bot settings button when you complete your settings.
If you enable this option, it will add another 10 points score towards your security meter. (Intermediate Security Level)
Internet Bots Troubleshooting and FAQ
Issue one: If you run into issues between Google bots, Yoast SEO, sitemap.xml file and or other IP issues then check the following URL Firewall Settings. Use one of the different global variables available in the settings under Advanced Settings tab.
Q1 Is there a list of IP address for fake Google bots?
Answer one: No, there is no list. The plugin has code in which it checks the useragent and the IP address and then it will get the internet hostname using the IP address. After that it will do a reverse IP lookup using the internet hostname calculated in the previous step. If the IPs match then the bot is considered legitimate. (Answer provided by wpsolutions)
=============================
404 detection
Step 7 ) Note: This has moved to Brute Force.
=============================
Blacklist
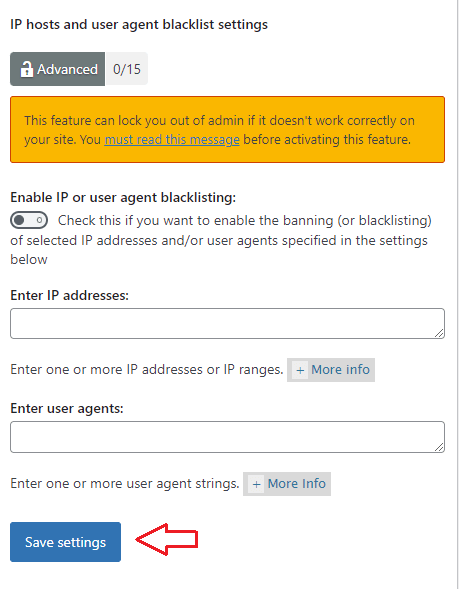
Step 8 ) Click on WP Security -> Firewall -> Blacklist to activate the following security settings.
IP hosts and user agent blacklist settings options
- Enable IP or user agent blacklist:
- Enter IP address:
- Enter user agent:
- Click on Save settings button when you complete your settings.
Troubleshooting Blacklist
Q1 I am having issues with the Black list feature. I think it is not blocking the IP address I add. What can I do to test this feature?
Solution 1: To confirm if the blacklist feature works try using your IP address to block yourself temporarily. Follow the steps below.(Solution provided by wpsolutions.)
Note: If the blacklist is working properly you will see a “403 Forbidden” error whenever anyone with a blacklisted IP address attempts to access your site.
1) Make sure you are logged into your server using FTP. This will be handy to unlock yourself if needed.
2) Log into WordPress admin panel and add your IP address to the blacklist settings.
3) Try accessing your site from a browser where you are not logged in. You should be denied access. If not, then the apache directives are not working on your server.
(If things are working fine and you do get blocked, just FTP your .htaccess file from your server to your computer and edit that file and remove the part of the code which has your IP address and then FTP the file back to the server)
Solution 2: Someone in the forum provided another solution if you are running a Bitnami WordPress installation. Check the following link support thread to learn more.
===============
Q2 Is there a limit to the number of IP addresses you can add to the Blacklist Manager in this plugin?
Solution One: No
===============
Q3 I’ve entered IP addresses into Blacklist Manager and checked the checkbox, but those IP addresses are still trying to log into the site. They also don’t appear in Dashboard => Permanent Block List.
Solution one: The “Permanent Block List” is not related to the “Blacklist Manager” feature.
The Blacklist Manager uses .htaccess rules and the permanent blocklist uses PHP. The permanent blocklist currently only allows the addition of IP addresses via the SPAM Prevention -> Comment SPAM IP Monitoring menu. (Solution provided by wpsolutions.)
FAQ
Q1 Where are the blacklisted IP addresses saved in the database?
Solution One: The blacklisted IP addresses are saved in the options table inside the “aio_wp_security_configs” option_name. You can read more about it in the following support thread.
=============================
WP REST API
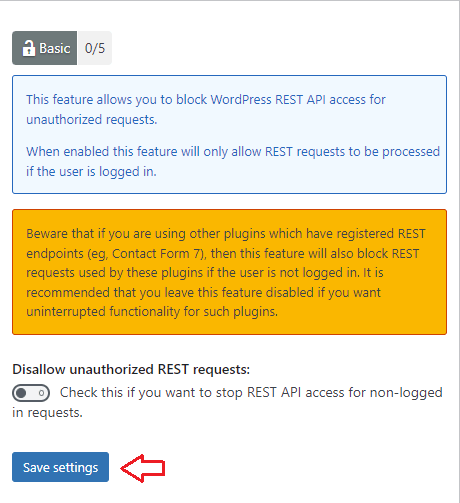
Step 9 ) Click on WP Security -> Firewall -> WP REST API to activate the following security settings.
Ip hosts and user agent blacklist settings
- Disallow unauthorized REST requests:
- Click on Save settings button when you complete your settings.
=============================
Advanced Settings
Step 10 ) Go to WP Security -> Firewall -> Advanced settings to set up or downgrade the firewall. Refer to the following link Firewall Advanced Settings to learn more.
=============================
That’s how easy it is to configure the firewall rules in aios.
Click on the following link Brute Force to continue configuring the plugins settings.
If you have any questions please let me know
Enjoy.
All In One Security (AIOS) Plugin Tutorial List