AIOS Plugin Pingback Protection Settings post shows you how to enable and check if xmlrpc.php file is working correctly in your website.
Last Updated: November 6, 2023
Latest News: Updated the documentation.
Too many keep reporting issues with their website receiving too many lock outs from various IP addresses. In some cases it might be one IP address that keeps finding a way to your websites admin login. The first step you should take is to enable one of the features found in the following link Brute Force features, like rename the login page. This will stop users from trying to access your admin login page.
If you still receive many logging attempts to your admin account, this could be because they are most probably targeting your xmlrpc.php file. This file can be found in the WordPress root directory of your site. Enabling one of the following features can help you reduce or stop further login attempts.
What you need:
AIOS Plugin Pingback Protection Settings
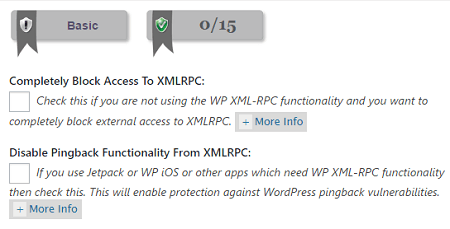
Step 1 ) Go to WP Security -> Firewall -> Basic Firewall Rules and enable one of the following security options as illustrated in the image below.
Basic Firewall Rules Features
- Completely Block Access To XMLRPC:
- Disable Pinback Functionality From XMLRPC:
Note: Make sure you click on More Info link as illustrated in the image below before you enable any of these options.
When you enable the following Complete Block Access To XMLRPC: you will see the following message appear in your admin panel. When you enable this feature you are blocking access to the following file xmlrpc.php. This file can be found in the WordPress root directory of you website installation.
(Attention: You have enabled the “Completely Block Access To XMLRPC” checkbox which means all XMLRPC functionality will be blocked.
By leaving this feature enabled you will prevent Jetpack or WordPress iOS or other apps which need XMLRPC from working correctly on your site.
If you still need XMLRPC then uncheck the “Completely Block Access To XMLRPC” checkbox and enable only the “Disable Pingback Functionality From XMLRPC” checkbox. )
Note: Only enable Completely Block Access To XMLRPC:, if you only log in through your website. Enable the other option if you access your website via other means like remote access etc.
When you enable Completely Block Access To XMLRPC: and you type the following yoursite.com/xmlrpc.php on the browser you should see the following message 403 forbidden apparently or something similar depending on how you have set up your website security.
If you don’t see the above forbidden message and you see the following message XML-RPC server accepts POST requests only, that means the xmlrpc.php file is still active and working in your site. That means that for some unknown reason it did not write the correct rules in your .htaccess file. In some cases you might have a plugin, theme or your server that controls and writes to xmlrpc.php file.
Note: The above does not apply if you enable the following option Disable Pinback Functionality From XMLRPC:.
=====================================
Troubleshooting XMLRPC
The following options allow you to troubleshoot and check to make sure the features above work in your site correctly. These steps are important to carry out to make sure it works, or else it defies the purpose of enabling one of the above features if it is not going to work in your site as expected.
Option 1 Disable the following option Completely Block Access To XMLRPC: and save the settings. Log out and then log back in and activate the Completely Block Access To XMLRPC: option again. Type the following yoursite.com/xmlrpc.php in your browser. You should see the following message 403 forbidden apparently.
Note: If the above did not work, carry on to the next Option 2.
=====================================
Option 2 FTP into your website and locate your .htaccess file (This file is located at the root of your WordPress install). Download .htaccess file locally to your computer/ laptop. Open the file with a plain text editor like notepad in windows and locate the entry rules listed below. If you don’t see these rules as illustrated below, then copy and paste the rules below into your .htaccess file. Save the file and upload it back to where you found it “in the root of your WordPress install” of your server.
#AIOWPS_PINGBACK_HTACCESS_RULES_START
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
#AIOWPS_PINGBACK_HTACCESS_RULES_ENDType the following yoursite.com/xmlrpc.php in your browser. You should see the following message 403 forbidden apparently.
Note: If the above did not work, carry on to the next Option 3.
=====================================
Option 3 Sometimes your file permissions might be incorrect. Click the following link file permissions to learn more.
If the file permissions link above does not help you, try the following steps.
- Edit your .htaccess file and remove the plugins entries.
- Save your .htaccess file and upload again to your server.
- Reinstall AIOWPS plugin and activate it. Make sure you say Yes to enabling the previous settings. This will write all the rules again to the .htaccess file.
- Then carry out a test.
If it is working correctly, it will stop anyone from trying to access your website via the xmlrpc.php file.
=====================================
I hope the above documentation helps you.
If you have any questions please let me know.
Enjoy.
All In One Security (AIOS) Plugin Tutorial List